Get ahead
VMware offers training and certification to turbo-charge your progress.
Learn moreUsing username/password credentials to access one application from another presents a huge security risk for many reasons. Today, we are announcing the preview of passwordless connections for Java applications to Azure database and eventing services, letting you finally shift away from using passwords.
Passwords should be used with caution, and developers must never place passwords in an unsecure location. Many Java applications connect to backend data, cache, messaging, and eventing services using usernames and passwords, or other sensitive credentials such as access tokens or connection strings. If exposed, the passwords could be used to gain unauthorized access to sensitive information such as a sales catalog that you built for an upcoming campaign, or simply all customer data that must be private.
Embedding passwords in an application itself presents a huge security risk for many reasons, including discovery through a code repository (see Figure 1 below). Many developers externalize such passwords using environment variables so that applications can load them from different environments. However, this only shifts the risk from the code itself to an execution environment. Anyone who gains access to the environment can steal passwords, which in turn, increases your data exfiltration risk.
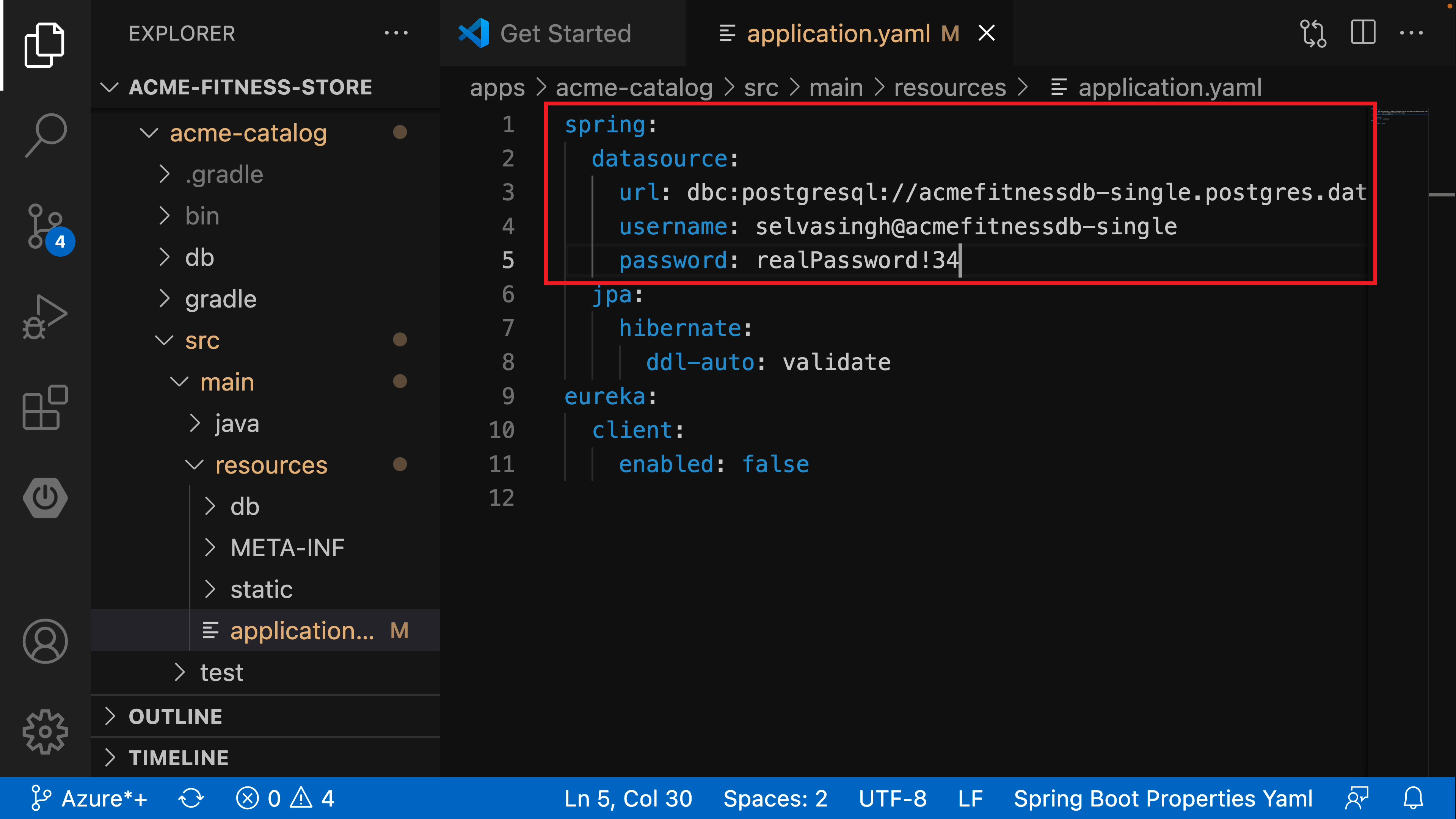
Figure 1 – shows Java code with an embedded username and password to connect to a database
Our customers can have strict security requirements to connect to Azure services without exposing passwords to developers, operators, or anyone else. They often use a vault to store and load passwords into applications, and they further reduce the risk by adding password-rotation requirements and procedures. This, in turn, increases the operational complexity and can lead to application connection outages.
Now you can use passwordless connections in your apps to connect to Azure-based services with a code-free configuration. You no longer need to rotate passwords. Using the principle of "never trust, always verify and credential-free", Zero-Trust helps to secure all communications by trusting machines or users only after verifying identity before granting them access to backend services.
Using managed identities and Azure RBAC (role-based access control) combination is the recommended authentication option for secure, passwordless connections from Java applications to Azure services. Developers or operators do not need to manually track and manage many different secrets for managed identities because these tasks are securely handled internally by Azure.
You can configure passwordless connections to Azure services using Service Connector (see Figure 2 below), or you can manually configure them. Service Connector enables managed identities in app hosting services like Azure Spring Apps, App Service and Azure Container Apps. It configures backend services with passwordless connections using managed identities and Azure RBAC, and supplies applications with necessary connection information – no more passwords.
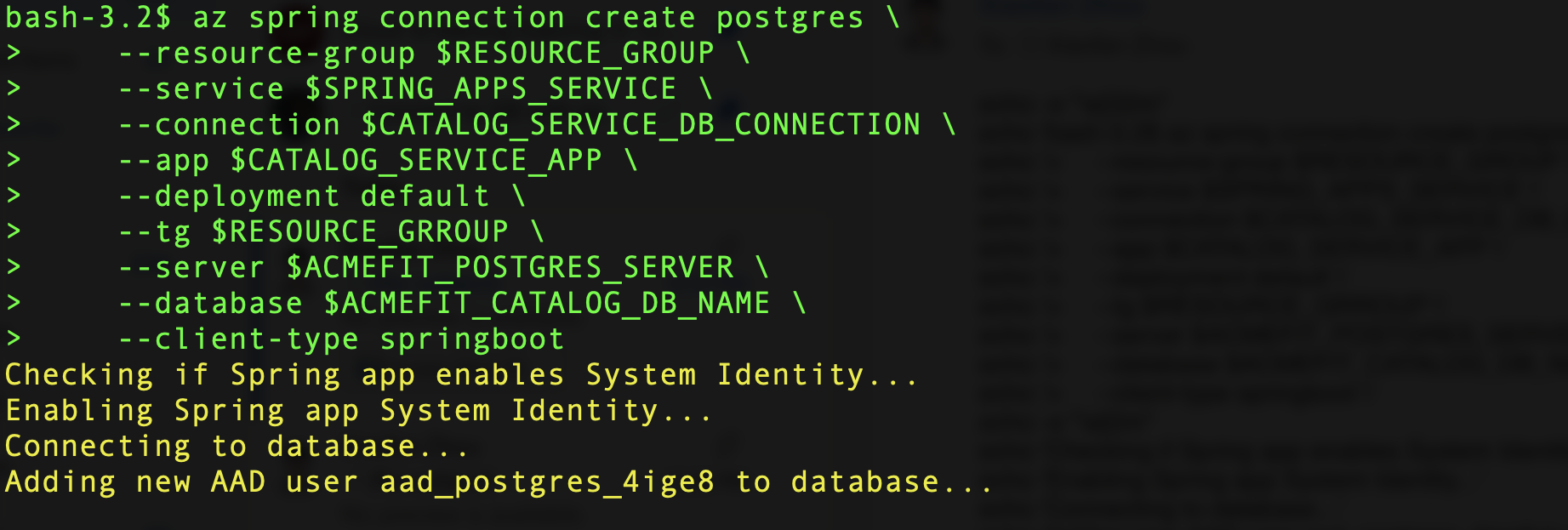
Figure 2 – Service Connector configures passwordless connection for a Java app to a PostgreSQL database
If you inspect the running environment of an application configured for passwordless connections, you can see the full connection string. For example, Figure 3 shows how it carries database server address, database name, and an instruction to delegate authentication to Microsoft’s Azure’s JDBC authentication plugin.
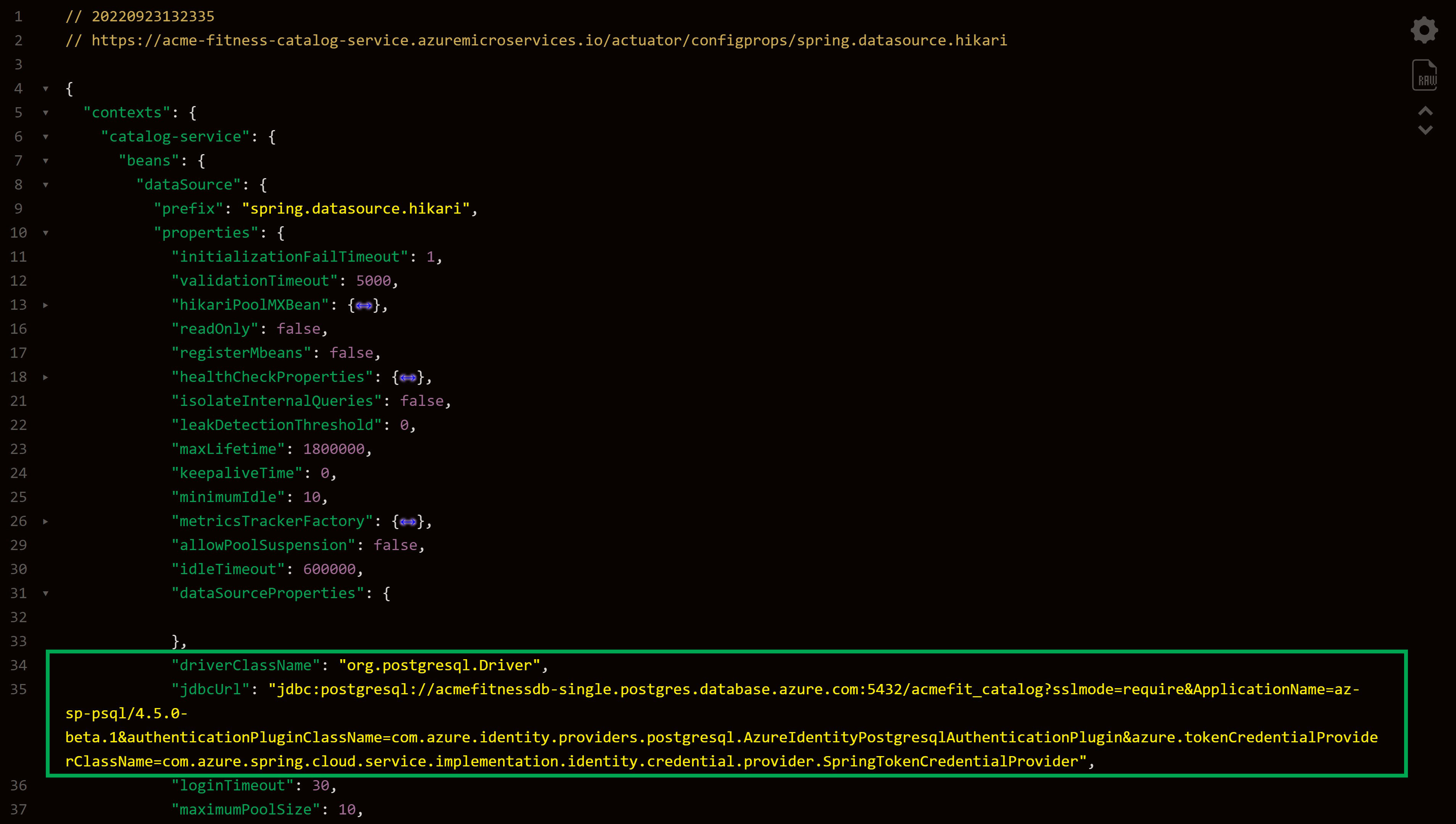
Figure 3 – datasource configuration “spring.datasource.url” shows passwordless connection
Let’s consider a Spring Boot application that connects to a PostgreSQL database that uses Spring Cloud Azure starter. The starter composes a connection string without password for a Spring Data JPA module. From the connection string, the driver understands that it must load the Azure’s JDBC authentication plugin which uses the Azure Identity Client Library to get an access token. The driver logs into a database using the token as password - no more passwords.
For local development and testing, developers can use the same arrangement to connect to services without using passwords. You will authenticate through Azure CLI, IntelliJ or any development tool and use that identity to secure access for the application to connect with Azure services without passwords.
You can shift away from using passwords in your apps. Migrate your existing Java applications to use passwordless connections for Azure services today!
Read more about passwordless connections – https://aka.ms/Delete-Passwords
You can use Service Connector to configure passwordless connections from Azure “compute” services such as Azure Spring Apps, App Service, Azure Container Apps, Azure Kubernetes Service and Virtual Machines to backend services:
| Service Connector | Azure Spring Apps | App Service | Azure Container Apps |
Check out this ready-to-deploy sample code for Spring Boot
Want to learn more about Azure Spring Apps and the ways you can leverage Spring on Microsoft Azure? SpringOne 2022 is almost here! I feel like it’s that anxious, exciting time before sort of important holiday where you get given gifts! And with it, Spring Boot 3 and Spring Framework 6. We’re going to be announcing everything right here on the Spring blog, of course, but if you want a chance to learn from the source, then I hope you’ll join us 6-8 December, 2022, right here in my hometown of San Francisco, my favorite west coast city in the USA, and my hometown. (Psst.: If you register now, there’s a $200 discount from the pass price with this code S1VM22_Advocate_200.)